Setup guide #Azure #KeyVault with Azure Active Directory Authentication
This guide helps you setting up Azure Key Vault, and using Azure Active Directory authentication to get the secret. Example how to use it in web apps or Episerver Forms.
Published 20th November 2017
Azure Key Vault helps safeguard cryptographic keys and secret. Anybody with an Azure subscription can create and use key vaults. Keys and secrets can be used in web applications and for example Episerver Forms.
First of all, before setting up the vault, to access the key vault, you’ll need to configure Azure Active Directory, register an app, and get credentials. What you need is an AppId/clientID and a key (access key), everybody who uses key vaults, whether users or applications, needs to be registered in Azure Active Directory.
Configure Azure Active Directory
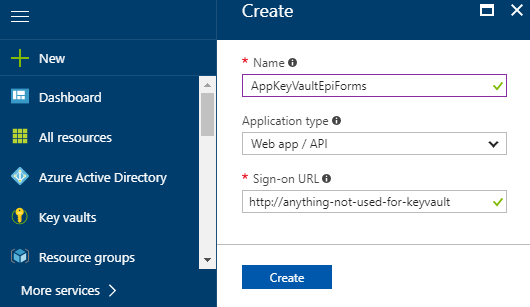
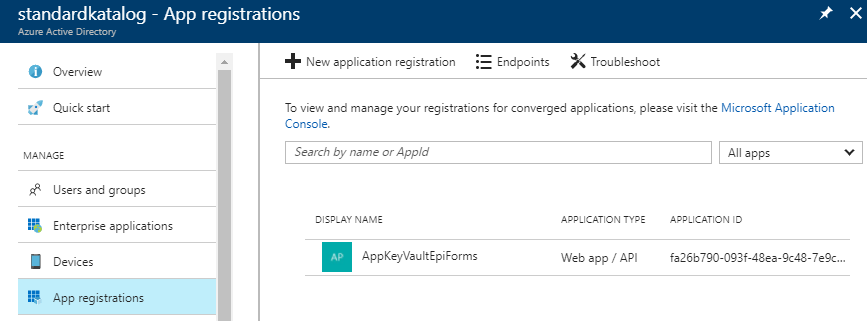
Go to Azure Active Directory > App registrations > Create
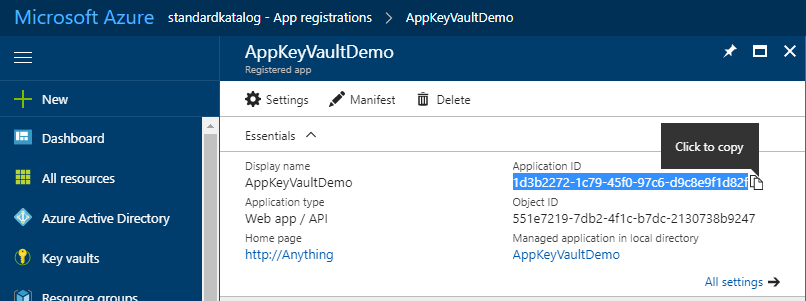 Retrieve the Application ID / Client ID
Retrieve the Application ID / Client ID
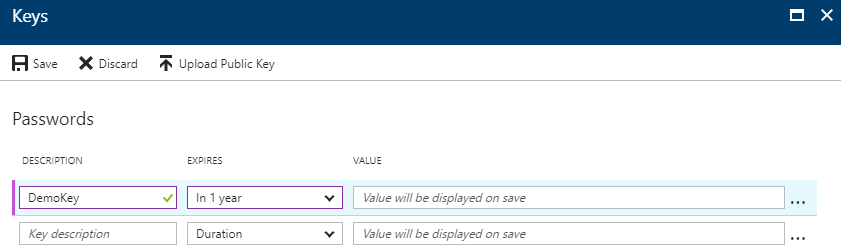
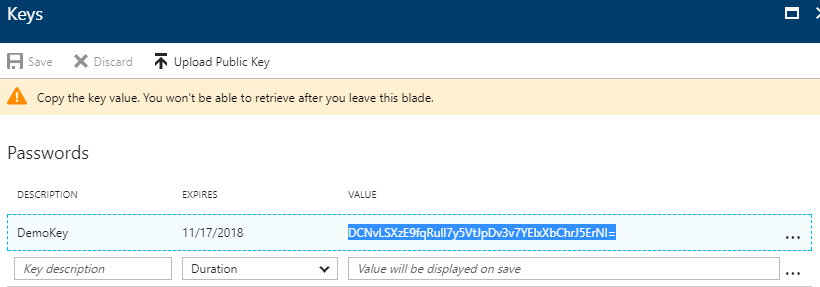
Configure AD Access key
Go to Azure Active Directory > App registrations > Your app > Settings > Keys
configure Key Vault
Go to Key Vaults > App registrations > Create
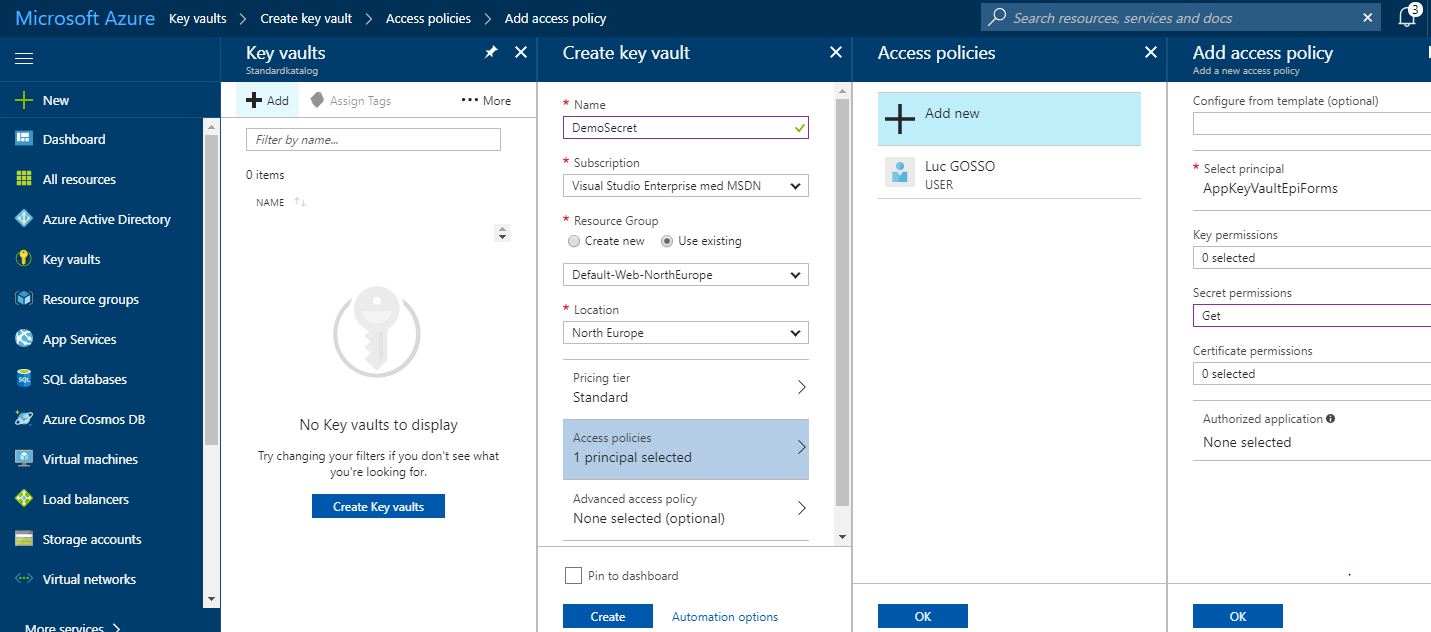 Important here is to register Access Policies > choose your new created App > Secret permission, choose GET.
Important here is to register Access Policies > choose your new created App > Secret permission, choose GET.
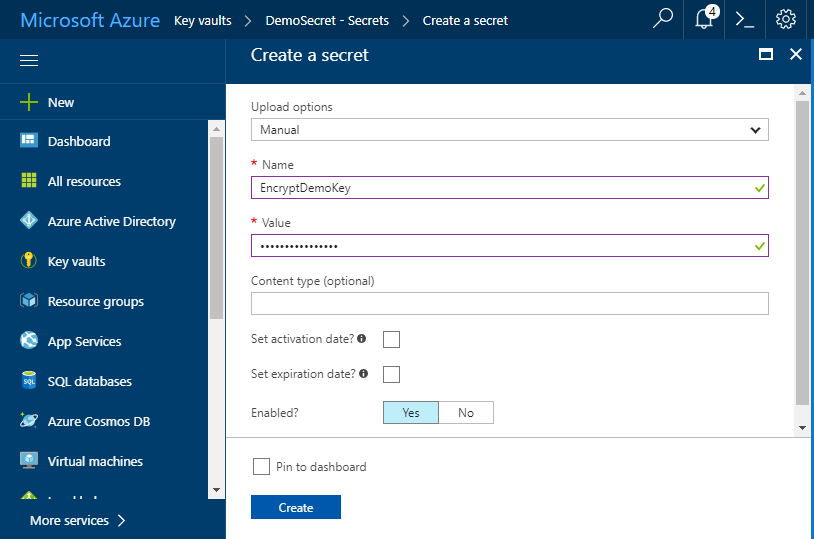
Create a secret
Go to Key Vaults > Your vault > Secrets > Create
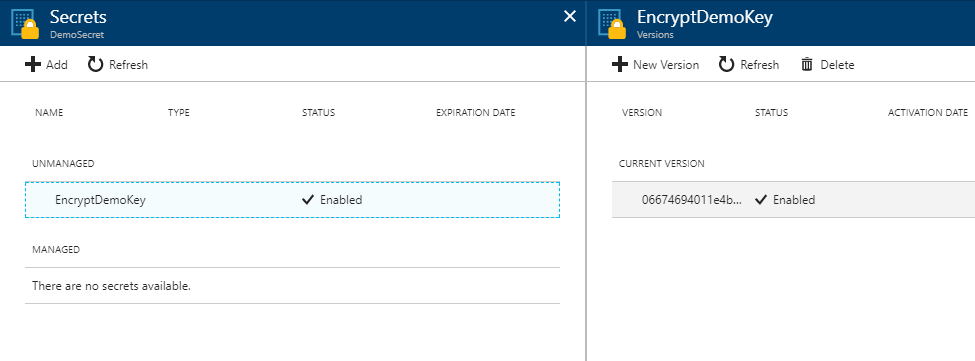
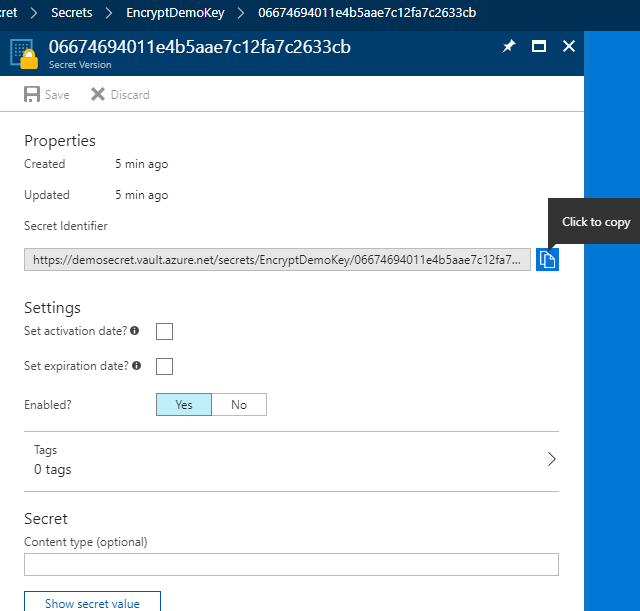 Retrieve your Secret Identifyer / KeyIdentifier: an endpoint url used for communication with Azure Keyvault.
Retrieve your Secret Identifyer / KeyIdentifier: an endpoint url used for communication with Azure Keyvault.
Thats it, now you got three things to communicate / retrieve Secret from Azure.
- ClientId: Application ID registered with Azure Active Directory
- ClientSecret: the secret created for the application.
- KeyIdentifier: the endpoint used for communication with Azure Keyvault.
Using key vault in a web application
Using Key Vault with Episerver Forms
Episerver Forms offers encryption of submission data, and uses Key Vault out of the box. To use the keyvault with Episerver Forms, you’ll need to install EPiServer.Forms.Crypto.AzureKeyVault in your solution
Episerver Forms uses the Advanced Encryption Standard (AES) to encrypt and decrypt data.
The secret should be base-64 encoded, meaning its characters are in the ASCII range of UTF8, and each character is 1 byte. So, the secret should contain only 16 characters for a key size of 128 bits, 24 characters for a key size of 192 bits, and 32 characters for a key size of 256 bits.
- Open the Forms.config file.
- Before the <providers> section, change to <storage defaultProvider=”DdsEncryptedPermanentStorage”> as provider.
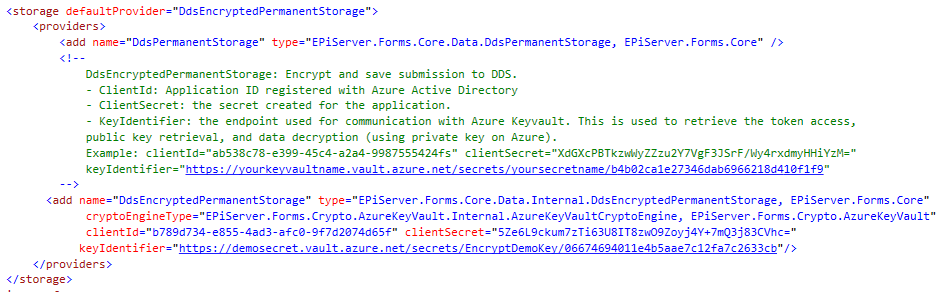
- Within the <providers> element, specify the three Azure KeyVault parameters for the cryptographic engine.
-
- ClientId. Application ID registered with Azure Active Directory.
- ClientSecret. The key created for the application in Active Directory.
- KeyIdentifier. The endpoint used for communication with Azure KeyVault. Used to retrieve token access, public key retrieval, and data decryption.
The Key Identifier looks like this (2017)
https://yourvaultname.vault.azure.net/secrets/yoursecretname/06674694011e4b5aae7c12fa7c2633cb
Resources
- https://docs.microsoft.com/en-us/azure/key-vault/key-vault-whatis
- https://blogs.technet.microsoft.com/kv/2015/06/02/azure-key-vault-step-by-step/
- https://docs.microsoft.com/en-us/azure/key-vault/key-vault-get-started
- http://world.episerver.com/documentation/developer-guides/forms/encrypting-form-data/
SEO Terms
- Azure AD, register app
- Error System.ArgumentException: Invalid ObjectIdentifier: Bad number of segments: 2
- Error System.ArgumentException: Invalid ObjectIdentifier: segment [1] should be ‘secrets/’, found ‘keys/’
- [KeyVaultErrorException: Access denied] Microsoft.Azure.KeyVault.<GetSecretWithHttpMessagesAsync>d__61.MoveNext()
- Microsoft.IdentityModel.Clients.ActiveDirectory: AdalServiceException: AADSTS70001: Application with identifier x was not found in the directory